Operation Crypto Redemption

Short intro
Thursday 16th Of March, Loganaden brought forward concerns about the recent vault7 release by wikileaks recently. We decided to spend this weekend making some patches. After trying to find out a name for the event, CV (name removed on request) came up with one. Soon one after the other, the different members came up with something. Kifah made our Poster and we were all set to start on Saturday.
What is vault7?
Vault7 is a series of WikiLeaks releases on the CIA and the methods and means they use to hack, monitor, control and even disable systems ranging from smartphones, to TVs, to even dental implants.
Thanks to Steven Chamberlain who initially noticed the issue in FreeBSD. The requirements mentioned in the wikileaks' article are part of the CIA's own internal infrastructure requirements.
8. (S//NF) Confidentiality must be provided by AES, Serpent, Twofish, Blowfish, 3DES, or RC4 with a minimum key size of 128 bits. Block ciphers must be operated in Galois/Counter Mode (GCM),Counter Mode (CTR), or Cipher Block Chaining Mode (CBC). If RC4 is used, at least the first 1024 bytes of the cryptostream must be discarded and may not be used.xxi AES is recommended due to hardware implementations by major CPU vendors and to enable transition to a more secure suite.
9. (TS//SI) Further than stated above, if RC4 is used the first 3072 bytes of the cryptostream must be discarded and may not be used.
What this means is that there is a high probability that there is someone or some organisations out there that have a practical attack on RC4 as it is currently being used. A long term solution is to switch to ChaCha20. By discarding more bytes (3072) of the first keystream, we reduce the possibility of non-random bytes (Randomness and Cryptography).
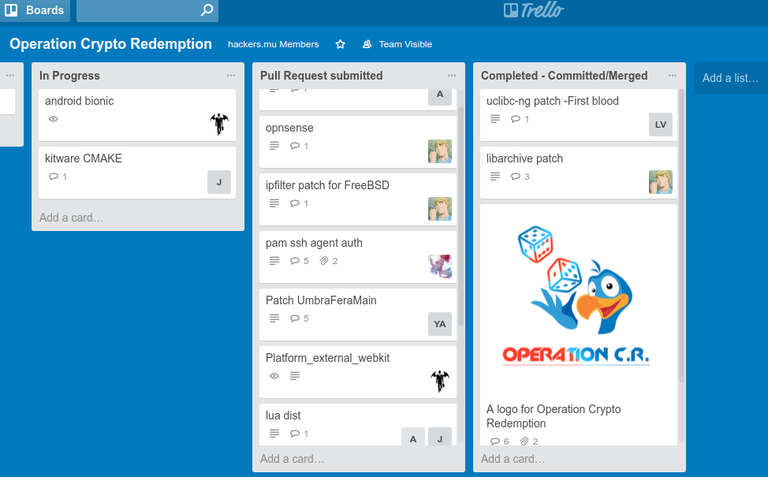
We discovered there were a lot of software out there that were using that specific implementation, and could do better that the requirement proposed. Hence we started making patches for them this weekend.
It was a nice team effort, everyone joined in and we planned everything on Friday night, we even had it laid out on our trello board and we started working on it as from Saturday. Soon by Sunday we managed to reached our planned target for the weekend and we were pleased we sent some patches to more projects than we initially anticipated.
| Participants | Project |
| Loganaden Velvindron | uclibc-ng |
| Pirabarlen Cheenaramen | webkit |
| CV (name removed on request) | libarchive, uclibc, opnsense, ipfilter, |
| Nitin Mutkawoa | lua dist, pfsense, kitware |
| Yash Paupiah | pam ssh agent |
| Akhil Maulloo | phantomJs |
| Yasir Aulear | FP Jumper, Prism Starter Kit, UmbraFeraMain |
| Sheik Meeran Ashmith Kifah | *Event's Poster |
With all these crazy revelations being made out these nowadays, it is important that everyone is constantly kept up to date with what is going on. I stress again on how important it is to never disregard any security issues, however minor they maybe, they can always be used in conjunctions with other flaws to end up causing a lot of harm and damages.
Expect the different members to write follow up articles on the project they worked on during the course of the week, follow us on twitter @hackersdotmu and on fb
Article is on defimedia also.(Note: The article is incorrectly titled as INFORMATIQUE : QUAND DES MAURICIENS DÉFIENT LA CIA, We and everyone here at hackers.mu has NOT in any way meant to 'defy' anyone, specially not any 3 letter agencies.)
Till then, happy hacking!
- Pirabarlen Cheenaramen